
15 Sep How M365 Defender can stop advanced cyberattacks with XDR and Automatic Attack Disruption
Cyberattacks are becoming more sophisticated and persistent, targeting organizations of all sizes and industries. Attackers use multiple techniques to evade detection, compromise systems, steal data, and disrupt operations. To defend against these threats, organizations need a comprehensive and unified security solution that can provide visibility, investigation, and response across the entire attack surface. Tools like XDR aim to help you to make the dwell time shorter. Dwell time in cybersecurity is a measure of how long a cyber attacker can stay hidden and active in a system or network before being detected and removed. It is calculated by adding the mean time to detect (MTTD) and the mean time to repair or remediate (MTTR) the attack. Dwell time is usually expressed in days, and it can vary depending on the type and sophistication of the attack, as well as the security capabilities and practices of the organization.
Tools like M365 Defender and Automatic Attack Disruption help you to stop attacks quickly by cutting off the connections of the compromised devices that the attacker is using to spread the attack. This can prevent them from reaching more devices and reduce the damage of an attack, from costs to productivity loss.
Did you know that Microsoft has a free eBook that shows how you can supercharge your security operations with XDR? Check the following link to download it: SCI XDR Ebook_v5_231205 (microsoft.com).
XDR
XDR – eXtended Detection and Response – is a SaaS tool that simplifies security by integrating different products and data. XDR helps enterprises deal with complex security challenges in multi cloud, hybrid environments. Unlike EDR, which focus on endpoints, XDR covers more products, such as servers, cloud apps, emails, identities etc. XDR also combines prevention, detection, investigation, and response, offering visibility, analytics, correlated alerts, and automated responses to enhance data security and fight threats.
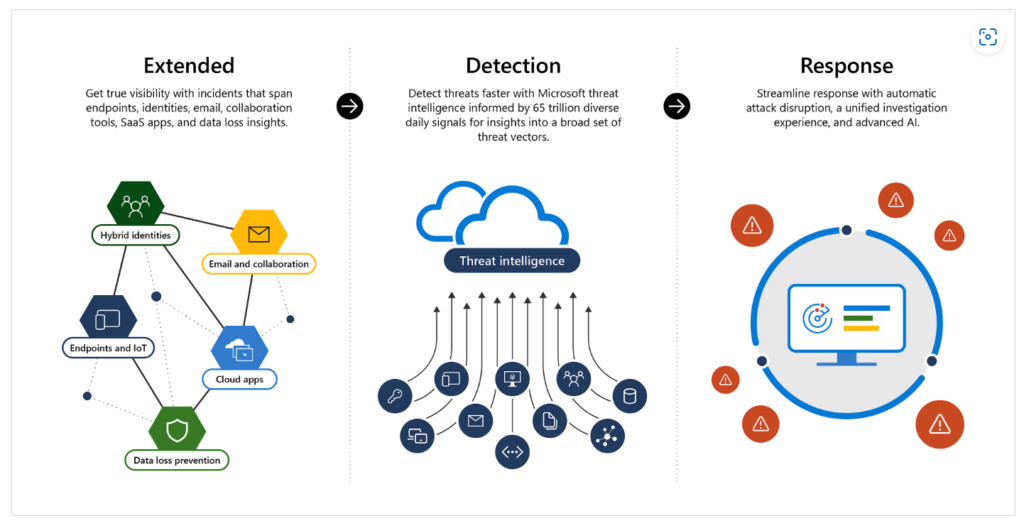
Image credits: Extended Detection and Response (XDR) | Microsoft Security
That’s where Microsoft 365 Defender comes in. Microsoft 365 Defender is an XDR solution that automatically collects, correlates, and analyzes signal, threat, and alert data from across your Microsoft 365 environment, including endpoint, email, applications, and identities. It leverages artificial intelligence (AI) and automation to automatically stop attacks and remediate affected assets into a safe state.
Unlike other providers that focus more on the endpoint side, Microsoft 365 Defender combines the signals from all Defender components to provide extended detection and response across the entire suite. This includes a unified incident queue, automated response to stop attacks, self-healing (for compromised devices, user identities, and mailboxes), cross-threat hunting, and threat analytics.
Some of the Key capabilities of XDR
- Correlated incidents
- Analytics
- Automated detection and response
- AI and machine learning
- Auto-healing of affected assets
Top XDR use case
- Detect endpoint device vulnerabilities
- Hunt threats across domains
- Investigate security events
- Perform endpoint health checks
- Predict future attacks
- Prioritize and correlate alerts
Automatic Attack Disruption
One of the key features of Microsoft 365 Defender is its Automatic Attack Disruption capability, which can contain attacks in real-time by containing affected assets that the attacker is using to spread the attack. This can limit the lateral movement and reduce the overall impact of an attack, from associated costs to loss of productivity.
To enable this capability, you need to have one of the Microsoft 365 subscriptions that include Microsoft 365 Defender, and deploy the relevant Defender products across your environment. You also need to configure the automation level for device groups and the automated response exclusions for users.
Once you have set up everything, you can view and manage containment actions in Incidents and the Action center in Microsoft 365 Defender. You can also review or change the settings as needed.
The image below shows you the yellow banner that is presented when the attack disruption took some action in the incident.
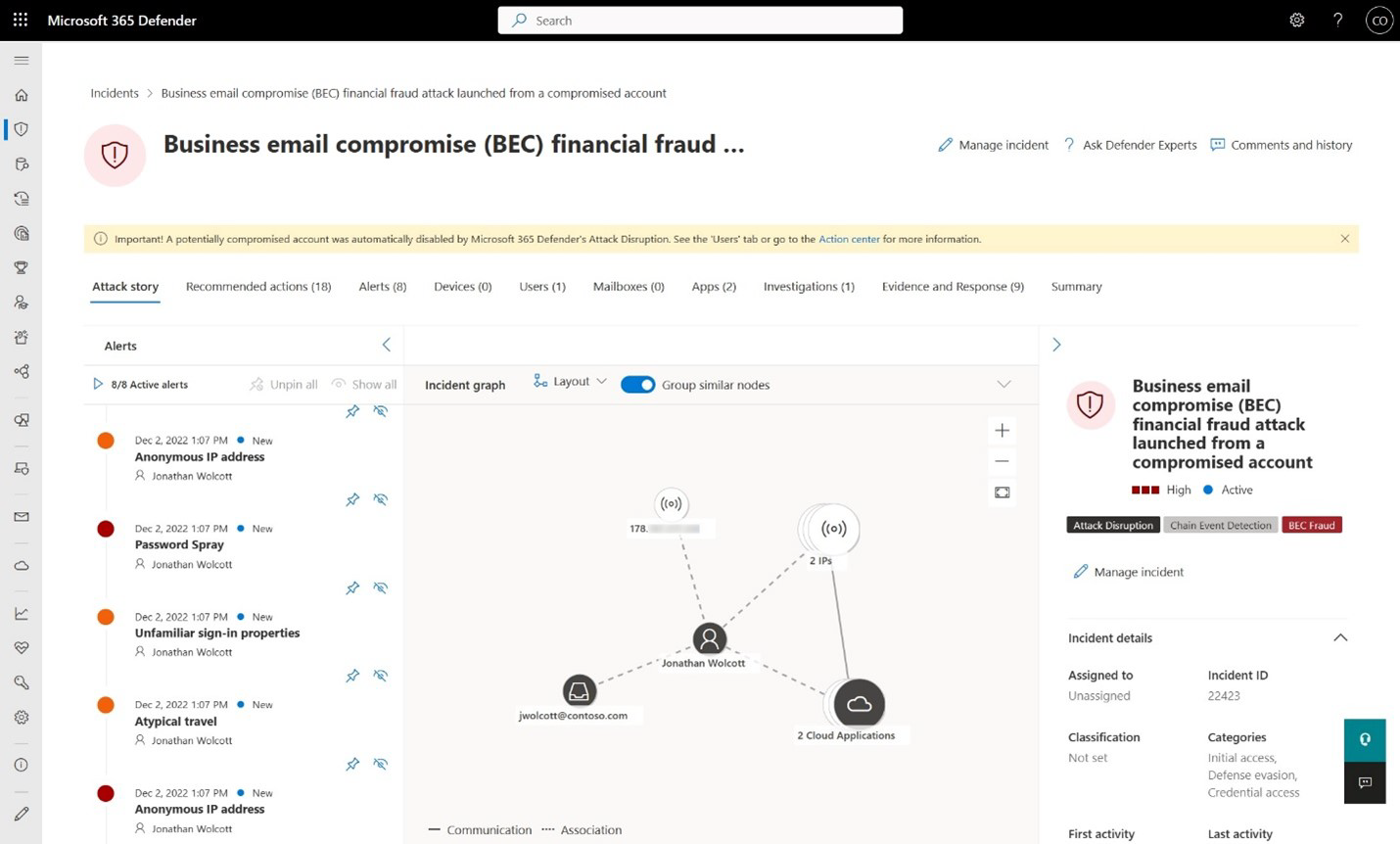
Image credits: Automatic attack disruption in Microsoft 365 Defender | Microsoft Learn
You can see additional visual cues to ensure visibility of these automatic actions across the Incident queue, Incident page or via API.
Prerequisites
This is a built-in feature and there is no option to enable it, but you need to check the prerequisites to run Automatic Attack Disruption in your environment:
Some of the scenarios where Automatic Attack Disruption can help you are:
- BEC (Business Email Compromise)
- AiTM (Adversary in The Middle)
- HumOR (Human Operated Ransomware)
Response Actions
I really like the way the Automatic Attack Disruption can take some response actions. I will list some of the actions below:
- Disable the user in Active Directory (needs the MDI sensors)
- Contain devices
- Revoke Entra ID user tokens
- Send Attack Disruption notifications
If you want to see the details and results of an automatic attack disruption action check this link: Details and results of an automatic attack disruption action | Microsoft Learn.
To learn more about how Microsoft 365 Defender can help you protect your organization from advanced cyberattacks with XDR and Automatic Attack Disruption, you can visit the following links:
- Microsoft 365 Defender – XDR | Microsoft Security: https://www.microsoft.com/en-us/security/business/siem-and-xdr/microsoft-365-defender
- Evaluate and pilot Microsoft 365 Defender: https://learn.microsoft.com/en-us/microsoft-365/security/defender/eval-overview?view=o365-worldwide
- Automatic attack disruption in Microsoft 365 Defender: https://docs.microsoft.com/en-us/microsoft-365/security/defender/automatic-attack-disruption?view=o365-worldwide
- How XDR defends against ransomware across the entire kill chain: How XDR defends against ransomware across the entire kill chain (microsoft.com)
- Ask the Experts: How XDR defends against ransomware across the entire kill chain: Ask the Experts: How XDR defends against ransomware across the entire kill chain (microsoft.com)
- Attack Disruption | Virtual Ninja Training with Heike Ritter: (999) Attack Disruption | Virtual Ninja Training with Heike Ritter – YouTube
- What’s new in SIEM and XDR: Attack disruption and SOC empowerment: What’s new in SIEM and XDR: Attack disruption and SOC empowerment – Events | Microsoft Learn
_



Sorry, the comment form is closed at this time.