
25 Apr Adapting for the new workplace with updates from Microsoft Purview Insider Risk Management
We recently shared how Microsoft insider risk solutions were evolving to meet the needs of the Great Reshuffle, including enhanced data exfiltration detection capabilities and richer alert context.
Today we announced Microsoft Purview – a comprehensive set of solutions which help you govern, protect, and manage your entire data estate. This new brand family combines the capabilities of the former Azure Purview and the Microsoft 365 Compliance portfolio that customers already rely on, providing unified data governance and risk management for your organization. Insider Risk Management in Microsoft 365 will now be called Microsoft Purview Insider Risk Management.
As part of this announcement, we are excited to announce the latest updates for Insider Risk Management:
- New policy recommendations, email notifications and sequence detection in analytics
- Policy triggers based on anomalous activity
- Detection capabilities for priority file types
- Expanded coverage with third-party alerts (via Microsoft Defender for Cloud Apps)
- Recommended guidance and actions for Insider Risk Management admins
- Launch of our new “Become an Insider Risk Management Ninja” resource page
New updates to analytics
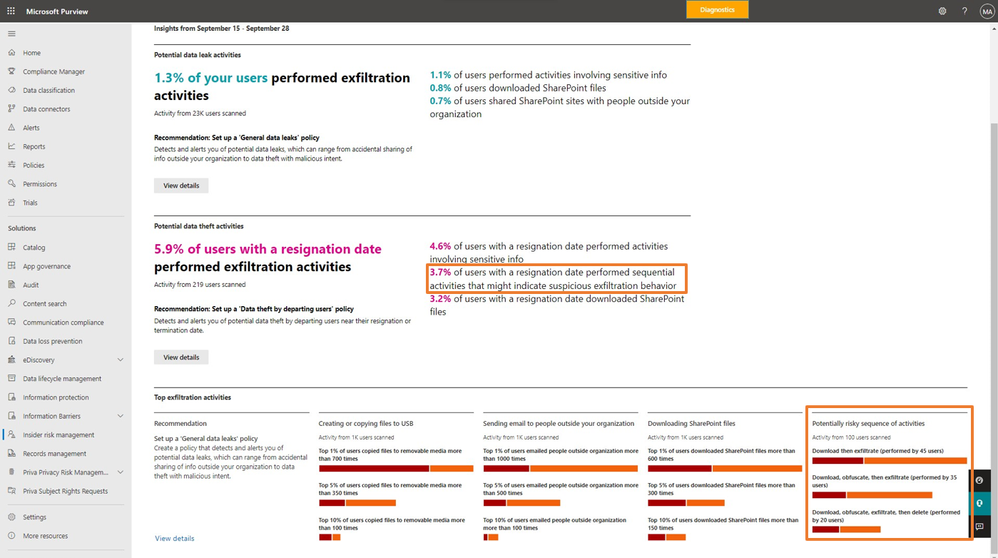
One of the best ways to get started with Insider Risk Management is with an analytics assessment. Within 48 hours of an Insider Risk Management administrator initiating the analytics assessment, the results provide actionable insights which may indicate risk of data leaks or theft, such as what percentage of users in your environment are performing exfiltration activities. These results are anonymized and aggregated, providing a top-level view of existing risks in your environment while protecting user privacy.
We are excited to announce that analytics will now be going further with new policy recommendations, email notifications and sequence detection capabilities in public preview:
- New policy recommendations: The results of an analytics scan will now include recommendations for policy thresholds, specifically built to address potential data leaks and IP theft. For example, if the analytics scan determines that your organization sends a large number of sensitive attachments to recipients outside of the organization, the recommended threshold for a data leak detection policy may be higher than in a typical organization. This helps security or compliance teams to set thresholds and policies that better reflect their organizations’ specific needs.
- Email notifications for analytics activation: We are now adding new email notifications so that Insider Risk Management administrators receive an email notification once analytics has been turned on and when the assessment results are first available.
- Enhanced insights with sequence detection: Identifying risky user behavior can be tricky when looking at isolated events, like confidential documents being sent to an external email recipient or downgrading a sensitivity label from “Highly Confidential” to “General”. When these events are tied together, however, security teams have more context and can better identify which activities pose a bigger risk. In Insider Risk Management, we refer to this as “sequence detection”: the activities may not raise alerts individually, but a flow of specific activities, like “Downgrade sensitivity level” > “Download” > “Exfiltrate”, may be something we want to flag as potentially risk activity. Analytics in Insider Risk Management will now include insights into the percentage of users who are performing sequences of risky activities, in addition to other data leak and exfiltration detection. (Learn more about sequences here: Investigate insider risk management activities)
New policy triggers based on anomalous activity
We are also further expanding Insider Risk Management’s ability to support organizations concerned about anomalous (or abnormal) activity. With our new anomalous activity policy trigger, security and compliance teams will have the ability to customize their policies to trigger on an anomalous activity, like an unusual amount of emails with attachments sent outside the organization, and bring users into scope of that policy.
This new capability means that Insider Risk Management can augment and support work done by security teams, by identifying what activities are abnormal or irregular for a user. Organizations looking to integrate more machine learning and automated decision making into their insider risk investigations may find that the anomalous activity trigger capabilities can help in identifying potential risks.
New detection capabilities for priority file types
When thinking about high-priority data or sensitive documents, your organization may have specific file types deemed particularly important. For example, an automotive company developing new car designs may create and save these designs in 3-D formats like .3dxml or .3mf. These files can be considered particularly sensitive due to the nature of their content, and organizations may want to prioritize these critical IP file types as high priority.
Insider Risk Management now allows organizations to indicate specific file types they would like to prioritize for additional visibility and scrutiny. Insider Risk Management administrators who are setting up new policies are able to indicate which file extensions should be considered high-priority, which can help in risk detection and surfacing important alerts.
Expanded coverage with third-party alerts (via Microsoft Defender for Cloud Apps)
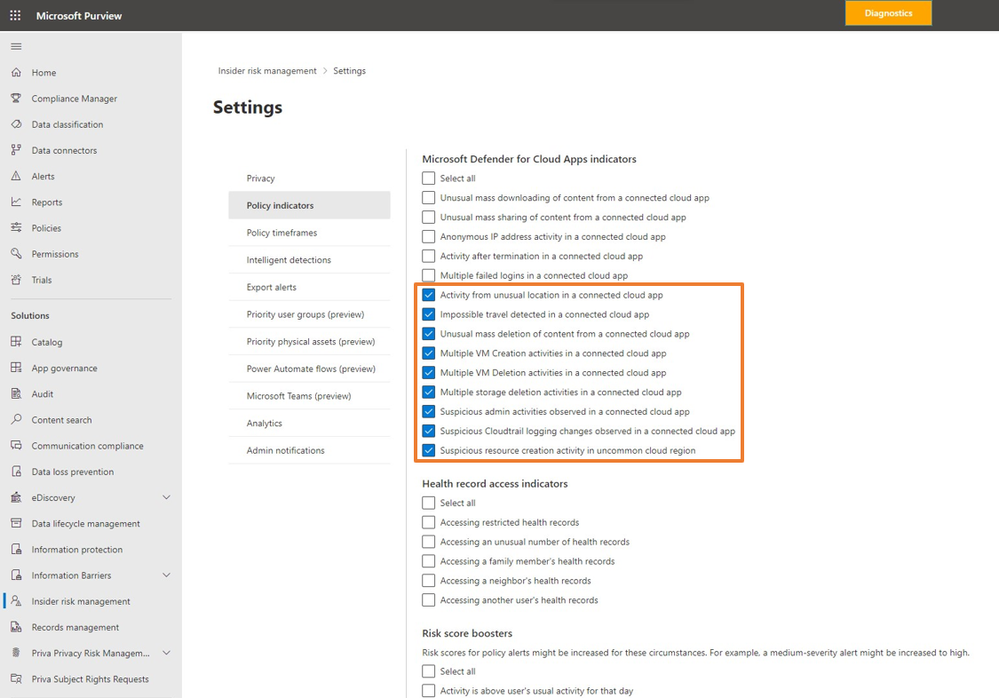
Insider Risk Management becomes even more powerful with alerts surfaced from third-party connected applications. We are now supporting nine additional third-party anomaly alert types via Microsoft Defender for Cloud Apps. These automatically enabled detection policies can detect and collate results, identifying behavioral anomalies across your users and devices in your network. Through this integration, Insider Risk Management expands coverage into multi-cloud environments including alerts identifying anomalous activity on Google Cloud Platform or Amazon Web Services, and allows organizations to have visibility if users are performing potentially high-risk activities like unusual mass deletion of content from a connected cloud app.
To leverage these capabilities in your policies, update your Insider Risk Management settings to include the “Microsoft Defender for Cloud Apps” policy indicators.
To learn more about anomaly detection policies in Defender for Cloud Apps, visit our Microsoft Docs page: Create anomaly detection policies in Defender for Cloud Apps.
Recommended guidance and actions for Insider Risk Management administrators
The best way to leverage the full capacity of Insider Risk Management is configuring the solution for your environment, your organizational requirements and your users.
Administrators are now more empowered than ever with guided recommendations for fine-tuning Insider Risk Management to fit their needs. These new recommendations are designed to help you to better manage noise from alerts in your environment, with recommended policy actions like adding domains, excluding specific file types or ensuring that all users are covered with at least one policy.
–






Sorry, the comment form is closed at this time.