
12 Apr Endpoint security reports in Intune admin center for tenant attached devices
We’re excited to announce that we’ve added data from tenant attached devices to the Microsoft Defender Antivirus reports in the Microsoft Intune admin center. These reports help you monitor your devices for status on malware and antivirus states.
With the release of Configuration Manager 2303 current branch, you’ll be able to opt into this feature with the option provided in the Cloud Attach Configuration Wizard properties.
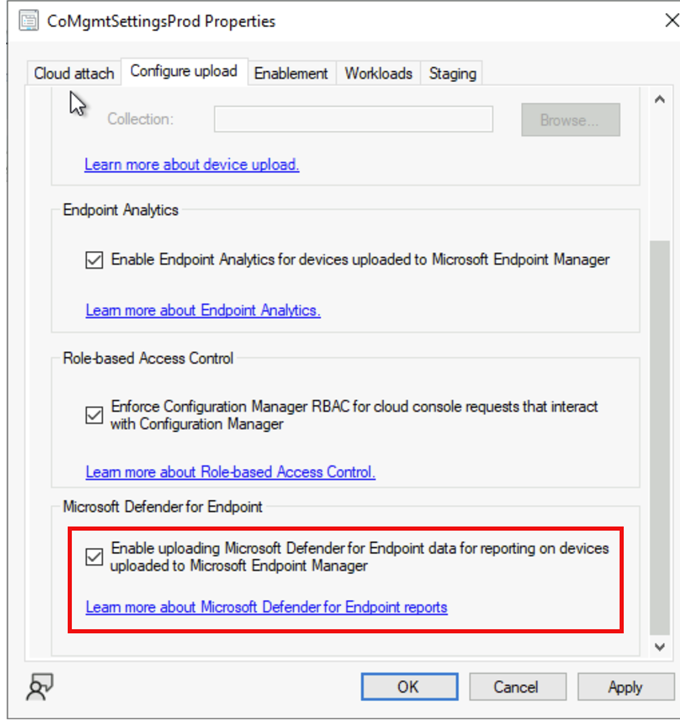
If you’re not cloud attached yet, sign up for this feature during Cloud Attach configuration wizard. Once you enable this feature in Configuration Manager, the data will become available after 4 hours. To learn more about Cloud Attach watch: https://aka.ms/cloudattach_video
Operational reports in Endpoint security
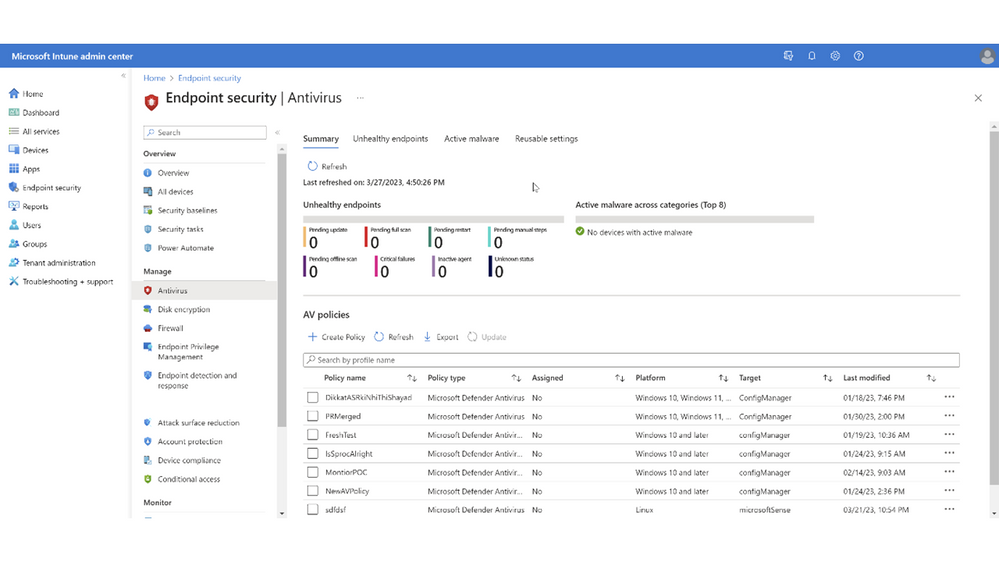
Under Endpoint security, you can navigate to Antivirus to see summary aggregates and operational reports to help you monitor the devices that need your attention.
The Summary tab provides aggregate information for the count of devices with a given threat agent status and the active malware category. With the Configuration Manager 2303 release, this chart will also include data from the tenant attached devices. Both aggregates show the top eight categories, which correspond to the operational reports on the other tabs. If there are no devices in any of the states, there will be no results to display.
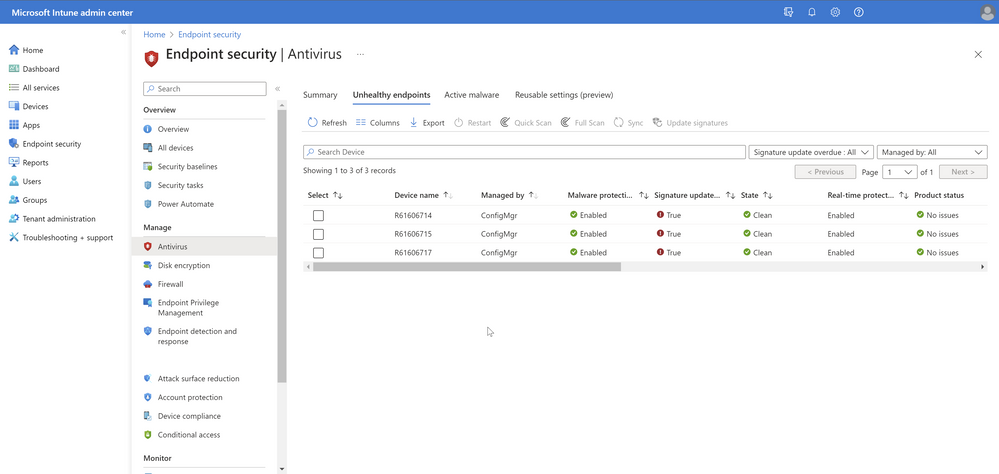
On the Unhealthy endpoints tab, you can view the operational report for the threat agent status on devices and users. Each record tells you whether malware protection, real-time protection, and network protection are enabled or disabled. You can view the state of the device and find additional information in the extra columns to help identify next steps for troubleshooting. Additionally, the Managed by column helps in sorting/filtering the devices based on the management mode, which includes MDM, Co-managed, or ConfigMgr (tenant attached devices).
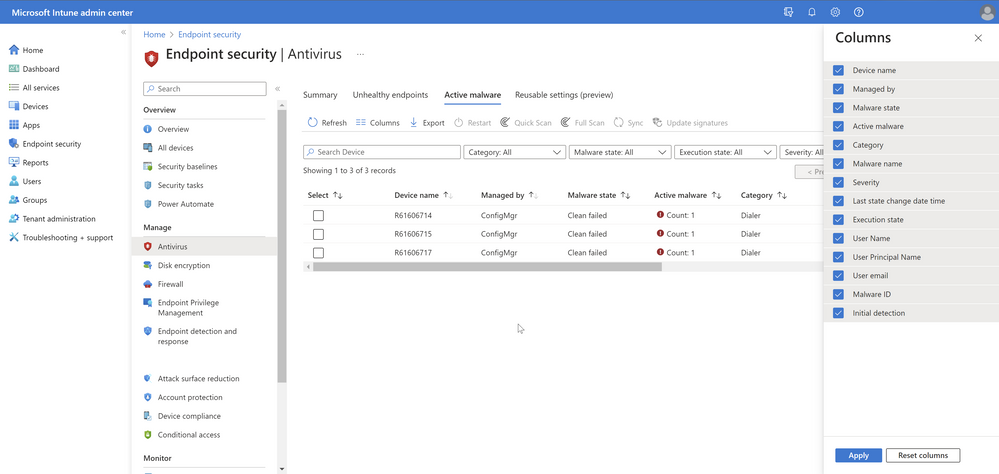
The Active Malware tab allows you to view the operational report to see the list of devices and users with active malware and includes details of the malware category. This shows the malware state and counts of malware found on the device. You can now filter the devices list based on Managed by (MDM, Co-managed, ConfigMgr and many more) and take remote actions including restart, quick scan, and full scan, or update signatures to help remediate your devices.
Note: Remote actions for tenant attached devices will be added soon.
Organizational reports in Endpoint security
Under the Reports option, you can navigate to the Microsoft Defender Antivirus report under Endpoint security to see summary and links to two existing organizational reports. The summary page and the reports are now updated to show data from tenant attached devices.
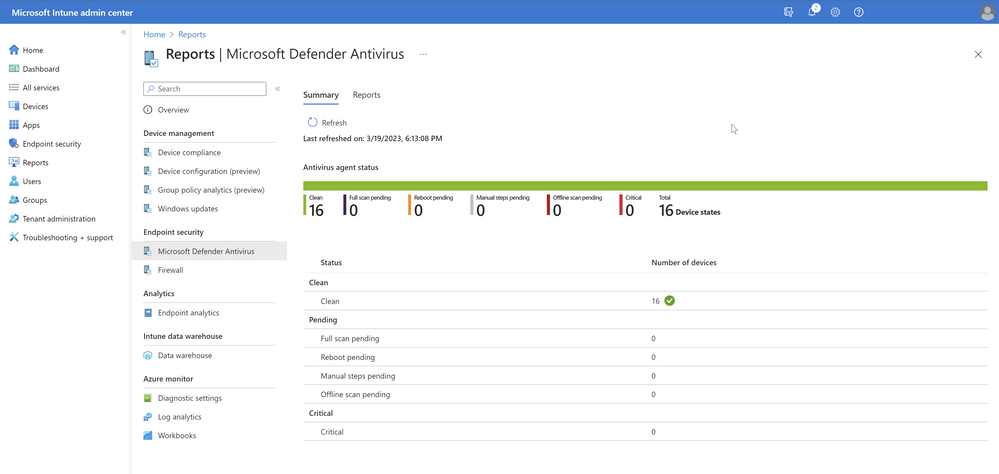
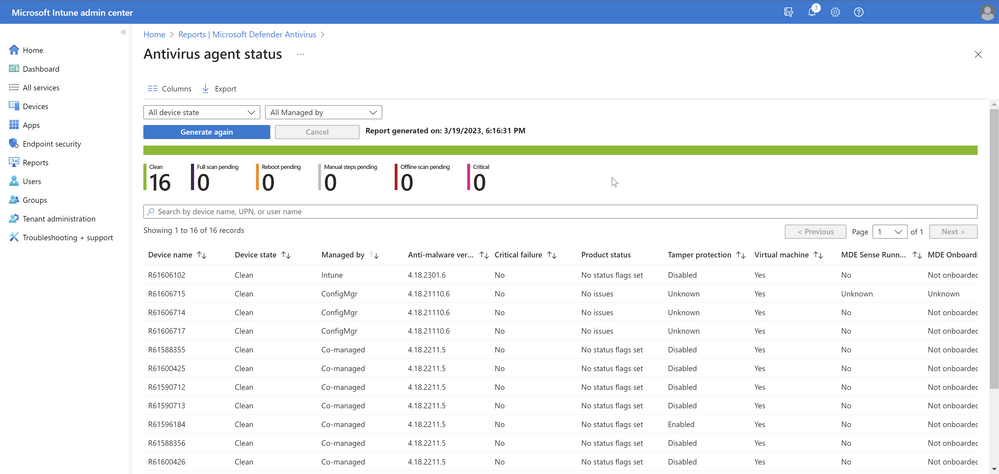
The first report, Antivirus agent status, allows you to generate a report to view the list of devices, users, and antivirus agent status information. Start by selecting the filter for the Device state (such as clean, critical, reboot pending, etc.) and/or the Managed by column (MDM, Co-managed, ConfigMgr) and other columns you wish to have in view. Once the report has been generated, a timestamp shows how fresh the data is. You can search across the results, sort, use paging controls, see the number of records, and export to a .csv file. The data within the report will remain in the admin center up to 3 days before requiring you to generate again.
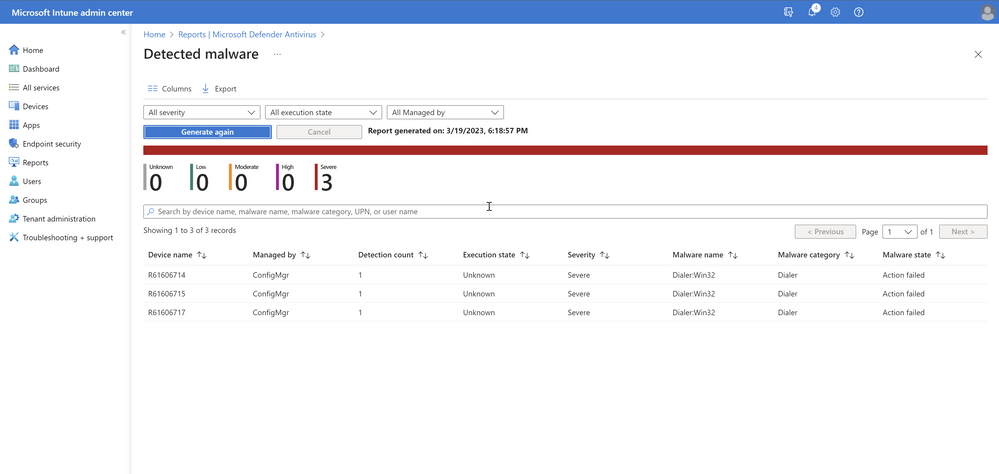
The second organizational report, Detected malware, works similarly in that you can select the filters for Severity, Execution state, and Managed by to generate your report. This report shows the list of devices and users with the count of detections, the execution state, the detection time, and the malware state/category.
To see a demonstration of the experience described in this blog, watch: https://youtu.be/QBbr-UzvxKg. For more information on these reports, see Tenant attach – Create and deploy Antivirus policies from the admin center.
_



Sorry, the comment form is closed at this time.